NSA Signals Intelligence (SIGINT)
National Security Agency/Central Security Service
THE SIGNALS NEED TO BE DECODED = THE "CSS" CENTRAL SECURITY SERVICES
NSA SIGINT can remotely detect, identify and monitor a person's bioelectric fields.
https://www.bibliotecapleyades.net/scalar_tech/esp_scalartech12.htm
National Security Act passed 1947 > CIA/ #NSA = #TI
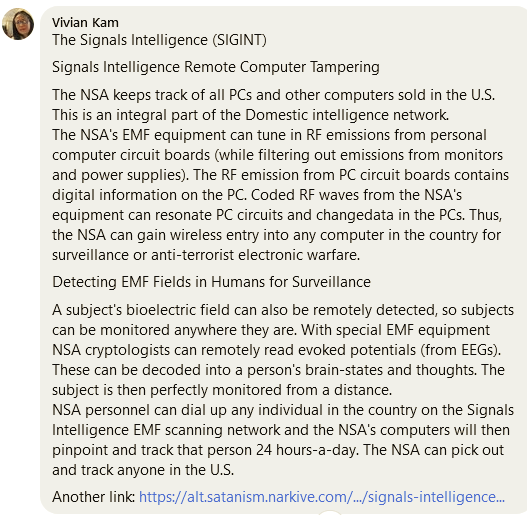
NSA keeps track of all PCs and other computers sold in the US.
https://alt.satanism.narkive.com/UnaUToj8/signals-intelligence-remote-computer-tampering
Confirms #FBI #CIA #NSA #ECHELON #Targeting / #Gangstalking of #TI's #V2K #RNM
https://www.targetedjustice.com/uploads/1/1/6/3/116323993/ted_gunderson_affidavit.pdf
Signals Intelligence #SIGINT
#NSA #ECHELON #FIVE-EYES > Secret Government > #MJ12
1) Primary Purpose Decipher & #Alien Communications
2) Monitor ALL Alien & Human Communications &
Contain the Secret of the Alien Presence. #MJ12
Project SIGMA Secret Government PAWNING Your Genome to Aliens! >>>> Project Sigma intercepted alien radio communications.
Project Plato Contact race of space aliens Ships >>>>
Project Plato was tasked with establishing diplomatic relations with this race of space aliens.
https://debatemindcontrol.webador.co.uk/royal-bloodlines-masters/treaties-with-aliens-see/project-sigma-secret-government-pawning-your-genome-to-aliens/project-plato-contact-race-of-space-aliens-ships
FOIA Complaint = Freedom of Information Act
Carnivore System = renamed DCS1000 (FBI) email electronic communications.
It used a customizable packet sniffer that could monitor all of a target user's Internet traffic.
Tempest System CODE NAME U.S. NSA NATO certification
referring to spying on information systems through leaking emanations,
including unintentional radio or electrical signals, sounds, and vibrations.
TEMPEST covers both methods to spy upon others and how to shield equipment against such spying.
Narus System



#NSA Signals Intelligence #SIGINT National Security Agency
THE SIGNALS NEED TO BE DECODED = THE "#CSS" Central Security Service
Find fix track target engage access Look Up Project Sigma / Project Plato 4 Out of this world info
Project SIGMA Secret Government PAWNING Your Genome to Aliens!
SEE MAIN PAGE CLICK IMAGE BELOW

https://media.defense.gov/2022/Apr/07/2002971965/-1/-1/1/2022_CCH_DIGITAL_CALENDAR.PDF
A Selection highlighted history... from link above... You may be better viewing link above...
NOT IN DATE ORDER! (MONTH ORDER FROM CALENDAR)
New Zealand warship captured Japanese submarine I-1, seizing multiple copies of JN-25 codebooks, 1943
BRUSA Agreement–U.S.-UK COMINT relationships during World War II, 1944
Arlington Hall Station (AHS), a former girls’ school, was headquarters for the U.S. Army’s cryptologic organization during and after World War II. The post also
served as one of the two main locations for the Armed Forces Security Agency from 1949 to 1952 and for the National Security Agency for several years afterward.
During the war, most AHS employees were women, like the keypunch operators gathered here on the campus.
Intelligence chiefs of U.S. Army and Navy established list of eligible readers of “Magic” intercept, 1941
North Koreans captured USS Pueblo, 1968 ?
In early 1944, the U.S. Army began hiring African Americans to do meaningful cryptologic work. Under the social mores of the time, their office was segregated.
In this photo cryptanalysts are working to break nongovernmental codes from multiple countries.
German spy Lothar Witzke arrested carrying a coded message, 1918 German Navy introduced 4-rotor ENIGMA for U-Boats, 1942
SIS began VENONA project, 1943 USAFSS received its first cryptologic units from the ASA, 1949
Colossus activated by Bletchley Park, 1944
The U.S. Navy’s OP-20-G moved to Nebraska Avenue, 1943
First Americans visit Bletchley Park, begins U.S.-UK cryptologic cooperation during World War II, 1941
Establishment of the 805th Signal Service Company for operation of the SIGSALY, 1943
Signing of King-Marshall Agreement— established role of Army/Navy COMINT liaison officers in Pacific theater, 1944
The ENIAC computer began operating, 1946
Government seizure of cryptologist Herbert O. Yardley’s tell-all memoir, Japanese Diplomatic Secrets,1933
Japan commenced operational use of the PURPLE machine-generated diplomatic cryptosystem, 1939
Station HYPO began reading Japanese system JN-25, 1942
BRUSA Communications Intelligence Agreement continues U.S.-UK partnership after World War II, 1946
U.S. Navy cryptologic organization redesignated OP-20-G, 1935
Evacuation of Station CAST from Manila Bay, 1942
CREAM replaced ULTRA as the codeword for top secret cryptologic material, 1946
First break into the Japanese Water Transport Code, 1943
The Yamato, a 72,000-tonJapanese battleship, sunk off Okinawa in large part because of SIGINT tipoffs, 1945
IBM introduces the System/360 mainframe computer, which developed from NSA’s HARVEST computer, 1964
FRUPAC intercepted encoded itinerary of Admiral Yamamoto Isoroku’s upcoming tour of the Solomon Islands, enabling his shootdown five days later, 1943
combination of COMINT and ELINT, 1962
U.S. Cyber Command established at Ft. Meade, with DIRNSA dual-hatted as its commander, 2010
Vice Admiral J. Michael McConnell, USN, became DIRNSA, 1992
What hath God wrought,” first telegraph message, sent from Baltimore to Washington, 1844
Prime Minister Baldwin revealed in Parliament that the British government had intercepted and decrypted Soviet telegrams
proving Soviet espionage conducted by the All- Russian Co-operative Society (ARCOS), 1927
Rum-running trial against Consolidated Exporters Corp. began with Elizebeth Friedman’s cryptanalysis of company’s encoded messages, 1933
Jargon code message announcing impending D-Day invasion intercepted and recognized by the German 15th Army but ignored at higher headquarters, 1944
U-505, with trove of German cryptographic material and devices intact, became first enemy warship, since the War of 1812, to be captured by a U.S. Navy boarding party, 1944
The USS Liberty, a Navy/NSA SIGINT collection ship, attacked by Israeli forces during the Six-Day War, 1967
Canada established its cryptologic bureau “Examination Unit,” 1941
Establishment of U.S. Army Code and Cipher Section, MI-8, 1917
Publication of Brownell Committee Report; laid foundation for establishment of NSA, 1952
Signal Intelligence Service took possession of Arlington Hall, 1942 NRO established, 1962
Communications Act of 1934 signed by President Franklin D. Roosevelt, 1934
USSR and U.S. agreed on hotline between Moscow and Washington, 1963
GRAB, first SIGINT reconnaissance satellite, launched, 1960
The “Potomac Code,” first of the AEF “River” series of field codes, issued, 1918
Albert J. Myer, developer of flag signaling system code, appointed signal officer with rank of major, 1860
Allies realized the U.S. diplomatic code had been broken by the Germans, 1942
CIA public ceremony for VENONA declassification, 1995
Cryptographic Security Board established, 1945
General Order 8 issued by AEF in France, establishing headquarters organization that included a cryptographic and cryptanalytic branch, 1917
First official public acknowledgment of NSA, 1957
Aaron Burr’s “cipher letter” to General Wilkinson intercepted, leading to charges of treason against Burr, 1806
The GUNMAN Project discovered implants hidden in typewriters used in the U.S. embassy in Moscow, 1984
Meeting at Pyry, outside Warsaw, where Poland shared its successes against the ENIGMA with Britain and France, 1939
JULY
National Security Act passed, 1947
#NSA Just what happened in 1947! = Everything Operation High-jump! Roswell! #MJ12 #CIA Both est... etc...
First use of transatlantic telegraph cable, generating upsurge in commercial cryptography, 1866
U.S. Navy Code & Signal Section established, 1916
The Soviets shot down an RB-50G-2 ?? >>> near Vladivostok, Russia, 1953
The AFSA, NSA’s predecessor, was the original centralized cryptologic organization in the United States; it was based at Arlington Hall Station and the Naval Security Station.
Australian Coastwatchers sent coded message noting sinking of John F. Kennedy’s PT-109, 1943
The “Mohawk” field code issued, 1918
Prototype U-2 made its first test flight, 1955
World Wide Web was launched, 1991
First World Wide Web page written, 1990
First public appearance of DIRNSA before Congress. Lieutenant General Lew Allen testified before the House’s Pike Committee, 1975
SecDef set the terms of reference for the Stone Board, which considered cryptologic reorganization after World War II, 1948
IBM introduced the IBM PC, 1981
Spy Velvalee Dickinson sentenced to ten years for providing intelligence to Japan via “Doll Code” steganography in messages, 1944
First transatlantic exchange of telegraph communications occurred with congratulatory messages between Queen Victoria and President Buchanan, 1858
NSA Far East (Tokyo) established, 1953
USCYBERCOM is elevated to a unified combatant command for cyberspace operations, 2017
“House of 4 Hats” dining facility for NSA military opened (later, House of 5 Hats), 1974
NSA responded to U.S. silver shortage in the 1960s by starting the NSA Silver Recovery Program to reclaim silver from scrap and waste, 1968 ?
President Eisenhower approves the development of the GRAB satellite system, 1959 ?
First meeting of the Stone Board; led to establishment of AFSA, 1948
Key intercepts of Russian radio traffic allowed German Generals von Hindenberg and Ludendorff to encircle and crush Russian forces at Tannenberg, 1914
Both the U.S. Navy and Army did vital communications security and cryptanalysis functions at their main cryptologic posts. Just prior to American participation
in World War II, the two services developed what turned out to be the most secure cipher machine of its time, called the “SIGABA” by the army and “ECM” by the
navy. Here, personnel are learning about the device. NSA Archives
First broadcast of the Star Trek episode “The Enterprise Incident,” loosely based on the capture of the USS Pueblo, 1968 ?
Genevieve Grotjan discovered the secret to unraveling the Japanese PURPLE machine, 1940.
President Obama visited NSA and USCYBERCOM, 2015
The Signal Security Agency reorganized as the Army Security Agency, 1945
First U.S. Intelligence Board meeting at NSA Fort Meade, 1966
President Reagan’s National Security Decision Directive-145 briefly gave NSA a role in securing data on federal computer systems, 1984
USAF Security Group established, 1947
British Major John Andre captured with treasonous ciphered letter from Benedict Arnold, 1780
The “Colorado” field code issued, 1918
Hubert H. Humphrey visited NSA; first vice-presidential visit, 1967
President Reagan dedicated Operations Buildings 2A and 2B; first presidential visit to NSA, 1986
USMC turned over responsibility for guarding NSA Fort Meade to Federal Protective Service, 1978
The American “Black Chamber” began operations, 1919 AFSA assumed operational control of cryptologic activities, 1949
SecDef announced that the Global Positioning System (commonly known as GPS) was complete; accurate to 100 meters, 1993
#NSA #Georgia fully operational, 1995 #Ukraine ? & Eu #Russia Border countries... #CIA ETC
A CRYPTIC HISTORY CALENDAR = WW2 ETC...
https://media.defense.gov/2022/Apr/07/2002971965/-1/-1/1/2022_CCH_DIGITAL_CALENDAR.PDF
TI are monitored "watched" & tracked 24/7 via technology example of CivvyStreet tech Radar Sensing in Assisted Living
#NSA = Signals Intelligence (SIGINT)
Please Learn about SIGINT & NSA - NSA is trying to make you Insane = I-NSA-NE
Delusional Change your thoughts & how U Think.
Every step you make - They R watching = #Illuminati ALL SEEING👁️!
Ted Gunderson AFFIDAVIT
- NSA TRANCE Formation of America - By Cathy O'Brien FREE PDF
- FIVE EYES TORTURER AND KILL THEIR OWN
- ECHELON REMOTE MIND CONTROL 1947 SECRET A&H SURVEILLANCE NETWORK
- GPS TARGETING HOW DOES IT WORK?
Project SIGMA Secret Government PAWNING Your Genome to Aliens! >>>> Project Sigma intercepted alien radio communications.
Project Plato Contact race of space aliens Ships >>>>
Project Plato was tasked with establishing diplomatic relations with this race of space aliens.
















































Create Your Own Website With Webador